In the world of rail freight operations, data security is crucial. At RSI Logistics, we prioritize keeping your data within Rail Command® safe and secure, and we place a heavy emphasis on strong security measures. In this article, we’ll explore our security practices, including compliance with Railinc’s authorization protocols, the advantages of using Azure for web hosting, our successful completion of the Type 2 SOC 1 Audit, and the impact these practices have on securing your rail freight operations.
Ensuring Secure Authorization with Railroads and Railinc
In today’s digital age, availability and access to accurate and secure data are pivotal in any sector, not least in rail freight operations. Ensuring secure authorization is therefore not just necessary, but critical, to securing your rail freight management.
The Mechanism of Authorized Vendor Access Within Railinc and how Rail Command® Ensures Security
Receiving and integrating Car Location Messages (CLMs) Event Sighting Codes into Rail Command® while simultaneously ensuring vendor access security involves a careful yet streamlined process.
First, the process requires the client’s authorization. This is achieved by having the client complete a letter that grants us access to their railcar trace data. After obtaining the necessary permission, we engage with the designated CLM provider. Following this, we set up the interface that links Rail Command® and the CLM provider, forging a secure connection. This established link makes it possible to securely receive sighting events in near-real time, enhancing visibility and efficiency for railcar tracking.
In the meantime, Rail Command® acts as the central repository for maintaining the client’s fleet of railcars. The CLM interface plays a pivotal role by allowing automated termination of sightings as cars are retired from the fleet, while initiating the collection of sightings for newly introduced cars.
Securing Rail Freight Operations with Railinc
On the other side, a significant part of this process lies in ensuring secure vendor access, squarely within Railinc’s Umler System. Railinc prescribes defined protocols for permitted access to the Umler System. Such access predicated on registration for a Single-Sign-On (SSO) account and enrolment for FindUsRail. Rail Command® unwaveringly adheres to this regulatory mechanism to assure that each user who obtains system access is both verified and compliant with the stipulated protocols.
The Umler System is capable of more than just access control; it hosts an advanced conflict management system. This system identifies and flags equipment records that conflict with supporting processes, another layer of scrutiny to maintain system integrity. Rail Command® utilizes this feature proactively, swiftly identifying and resolving any such conflicts or discrepancies in access. Thus, maintaining a secure vendor access environment.
The Significance of Robust Security Policies in Only Allowing Access to Authorized Vendors or Third Parties
Possessing robust security policies is paramount in today’s vulnerable cybersecurity landscape. By strictly allowing only authorized vendors or third-party entities to access data, Rail Command® significantly mitigates potential data breaches, preserving the integrity of the freight data and clients’ trust.
Upholding stringent security policies that align with Railinc’s authorization process is central to our ethos. We strictly adhere to these practices and are dedicated to continuously enhancing them to remain at the forefront of cybersecurity standards in rail freight operations.
Benefits of Web Hosting on Azure in Securing Rail Freight Operations
To complement our stringent security measures at Rail Command®, we’ve incorporated a multitude of Azure’s robust security offerings into our infrastructure. Microsoft Azure, a leading cloud hosting service, has emerged as an essential ally in our mission to create a secure, trustworthy, and reliable environment for rail freight operations.
Azure’s Robust Security Offerings
One of the key security advantages of Azure is the protection it provides against cyber threats. In an era where data is a valuable asset, Azure employs cutting-edge security measures to protect against data breaches.
Azure’s security is compliant with the stringent International Organization for Standardization (ISO) information security standards and adheres to compliances like the Content Delivery & Security Association (CDSA), Criminal Justice Information Services (CJIS), and DoD Information Assurance Certification and Accreditation Process (DIACAP). Furthermore, Azure safeguards data with its multi-layered protection. Much like a digital vault, all data stored in the Azure cloud is encrypted. This encryption ensures that only authorized entities, like Rail Command® and the system’s users, can decrypt and utilize the information, presenting considerable hurdles for unauthorized users.
Moreover, Azure’s resilience to unexpected disasters adds another layer of protection. Azure backs up data across multiple servers in various locations, safeguarding it from natural disasters and hardware failures. In addition to preserving data integrity, this redundancy significantly reduces recovery periods, minimizing downtime.
Rail Command®‘s Leveraging of Azure’s Capabilities
We harness the power of Azure to create a safe hosting environment for our rail freight operations platform. We transmute Azure’s state-of-the-art security capabilities into tangible advantages for our clients.
Azure’s scalability feature allows us to automatically adjust resources based on web traffic, securing the platform from crashes due to peak loads and helping us avoid unnecessary expenses during lulls. This feature works hand-in-hand with the robust protective measures Azure provides against cyber threats to maintain data security. In addition, Azure’s disaster recovery preparations have empowered us with a robust solution to safeguard our client’s data.
Our collaboration with Microsoft Azure bolsters our security posture at Rail Command®, reinforcing our mission to provide an unmatched, secure rail freight operations solution. By leveraging Azure’s dynamic capabilities, we safeguard user data, enhance platform stability, and ensure our commitment to client trust remains unswerving.
Type 2 SOC 1 Audit: Verifying Rail Command®‘s Compliance
Navigating the rigors of data security in today’s complex digital landscape necessitates comprehensive checks and controls. One mechanism that reinforces our commitment to robust security practices at Rail Command® is the Type 2 SOC 1 audit, a testament to our adherence to industry-standard best practices.
Significance of a Type 2 SOC 1 Audit
The Type 2 SOC 1 Audit, formally known as the “Report on Management’s Description of a Service Organization’s System and the Suitability of the Design and Operating Effectiveness of Controls,” is an internationally recognized auditing standard that ensures security processes are not only in place but are also effective over time. It evaluates the design and operation of a company’s controls over a period, typically six months. Compared to a Type I report, it offers a more rigorous and intensive audit reflecting long-term commitment to security, efficiency, and accountability.
Achieving a successful Type 2 SOC 1 Audit is a significant accomplishment, reflecting the organization’s rigor in protecting its systems and data. It enhances stakeholder confidence, leading to stronger and lasting professional relationships.
Success of Rail Command® in the Type 2 SOC 1 Audit
Rail Command®‘s commitment to excellence and superior data protection measures has led us to successfully meet the criteria for the Type 2 SOC 1 Audit. This audit evaluated our security controls over a specified period, in which our systems exhibited consistent compliance and effectiveness. With rigorous evaluation and our positive results, we have demonstrated our robust risk management systems and dedication to maintaining secure and efficient rail operations.
Continuous Commitment Amid Regulatory Changes
As security threats evolve and regulatory standards shift, it is imperative that we stay on top of changes and adapt accordingly. Therefore, we will continue to review and enhance our security protocols in line with the latest regulatory changes. This commitment reflects our dedication to ensure Rail Command® remains a trustworthy and secure solution for rail freight operations. It is our promise that we will never cease in our pursuit of safeguarding your data and maintaining the highest level of operational effectiveness. As your trusted partner, we ensure that our systems and processes will always stay ahead of the curve, reliably protecting your freight logistics data.
Choosing Rail Command®: Securing Your Rail Freight Operations
Rail Command® employs stringent authorization protocols, underpinning a resilient fortress against unauthorized access and data breaches. Our authorization matrix is designed to grant minimal, necessary access to users, ensuring a tight rein on data visibility, while maintaining operational efficiency. In essence, a tailored approach so that your business runs smoothly without compromising security.
Backing up this high-level security is our hosting partner, Azure. With Azure, Rail Command® enjoys robust, cloud-native protections including encryption, threat intelligence, and proactive risk management. These benefits translate directly into our users’ experience, creating a secure environment that enhances performance, while alleviating the pressure of security concerns — a testament to our solution-oriented approach.
Demonstrating our commitment to securely manage customer data, Rail Command® has successfully achieved the Type 2 SOC 1 Audit. This notable achievement is a testament to our rigorous adherence to internationally recognized best practices for data management and protection. As your knowledgeable partner in rail logistics, we understand the importance of trust in a successful partnership and are eager to provide this peace of mind to our users.
In the intricate world of rail logistics, our software ensures that you are navigating with a reliable, secure compass – Rail Command®.
Our commitment to operational security, efficient authorization protocols, robust hosting benefits and regulatory compliance are the cornerstones of our commitment to securing your rail freight operations. As rail professionals, we know how important it is that your rail freight management solutions integrate the industry’s best practices in data management and protection. Securely steering your operations with Rail Command® ensures that you are allied with a reliable partner – a partner that not only remains at the top of cutting-edge technology but also firmly anchored in the realm of uncompromising security and steadfast trust.





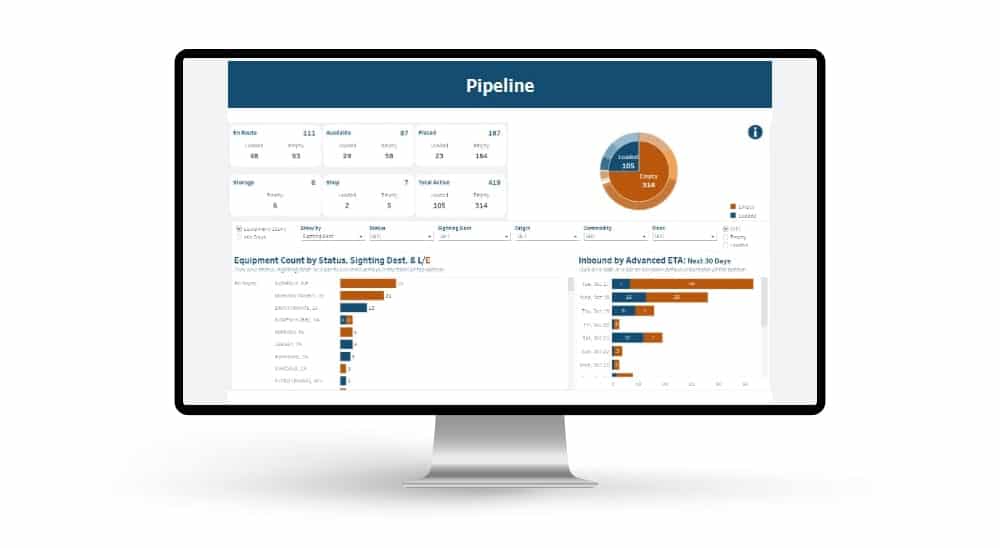 Automated exception reporting of the railcar tracking data makes it easy to identify and troubleshoot jeopardized shipments, thereby enabling you to provide better service to your stakeholders.
Automated exception reporting of the railcar tracking data makes it easy to identify and troubleshoot jeopardized shipments, thereby enabling you to provide better service to your stakeholders.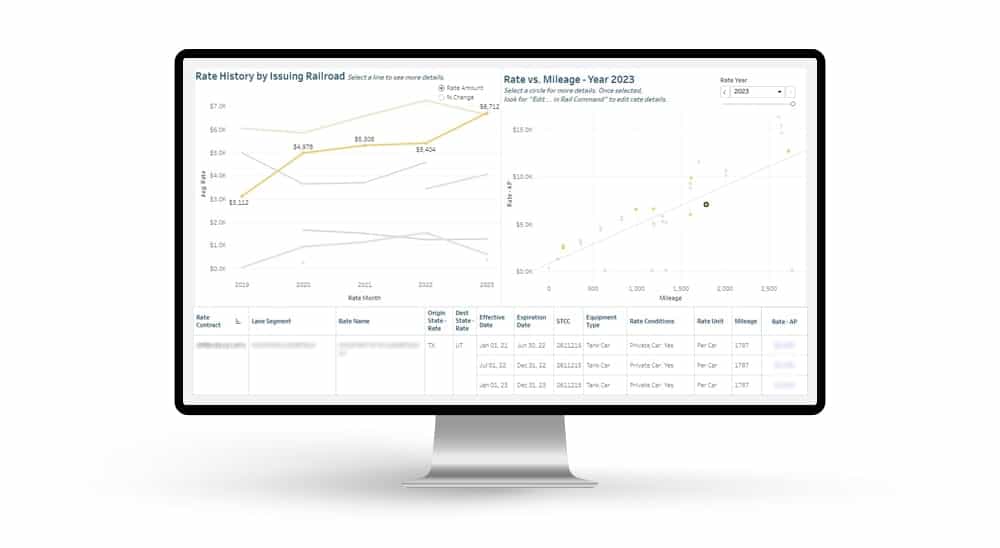 Receive notification of pending rate expirations. Tariff changes and fuel surcharges can be automatically updated.
Receive notification of pending rate expirations. Tariff changes and fuel surcharges can be automatically updated.